In a previous post, we talked about how MSPs should adopt a cyber protection plan enforcing elements featured in the Prevention and Detection stages.
MSPs can continue on a successful cyber protection path by next focusing on Stage 3: Response. Enable quick action to minimize risk by facilitating the following elements:
- Block malware execution. Protect users from inadvertently executing malicious files and scripts, including fileless attacks.
- Device isolation. Prevent devices connected to a network from accessing other resources connected to the same network (or other networks) once a compromise has been identified.
- Incident response. How quickly and effectively an organization responds to data breaches will determine the financial and reputational damage it faces.
- Alerts and notifications. These warnings provide timely information about current security issues, vulnerabilities, and threats.
- Network security. Centralized management of network security infrastructure will enable visibility into network-wide traffic and threats to secure access, protect users and applications, and control data from anywhere.
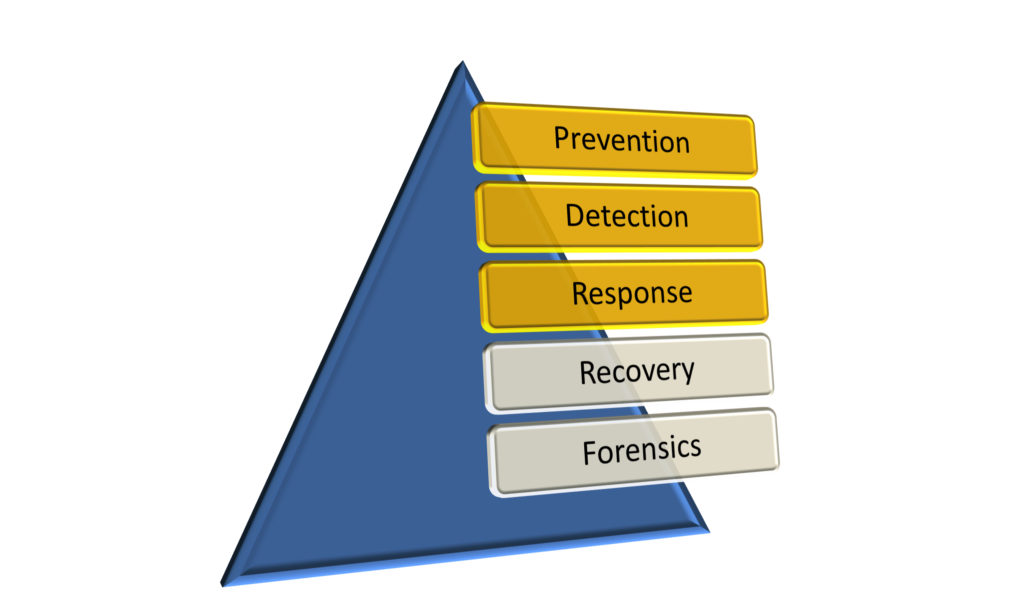
As technology leaders, it is imperative that MSPs have adequate plans for cyber detection and prevention in place, as well as response plans that work to minimize any potential damage from a breach.
Share via:
Tags: