In our series of posts on Cyber Protection for MSPs, we talked about how MSPs should adopt a cyber protection plan enforcing elements featured in the Prevention, Detection, Response, and Recovery stages.
MSPs should culminate their cyber protection journey by lastly focusing on Stage 5: Forensics. Mitigate future risks by collecting and performing forensic investigations with the following elements:
- Full data backups. Capture all data from source devices (computers, mobile phones, tablets, etc.) forensically so that all original data is in an unaltered state.
- Forensic data in backups. Capture a memory snapshot including the state of all running processes together with the backup.
- Endpoint detection and response (EDR). Perform root cause analysis to identify the origin of compromise and infection path.
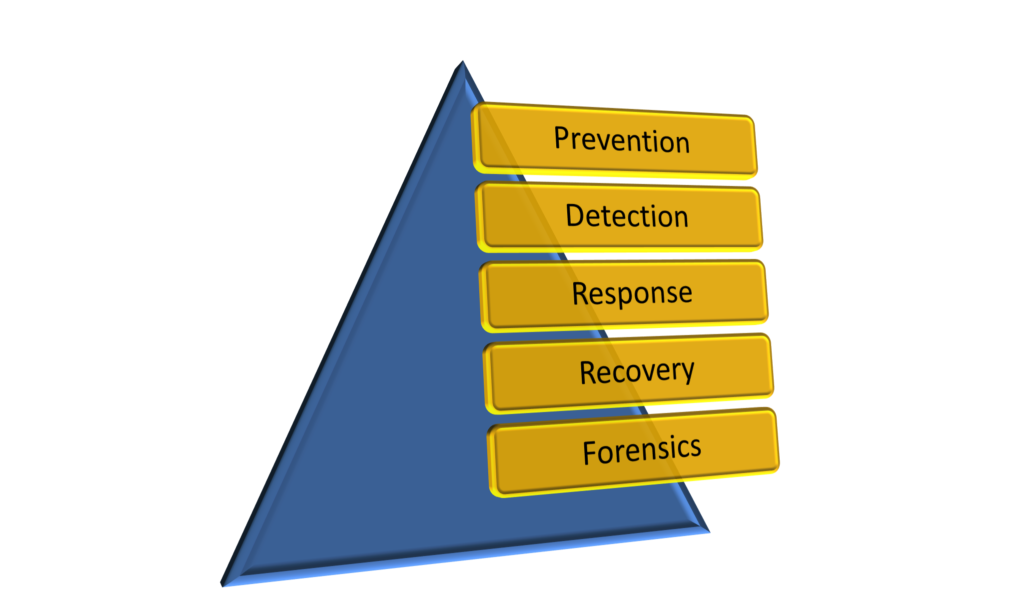
Proactively protect important business data from today’s advanced risks and threats as well as continuously adhere to an effective cyber-protection plan by implementing and following the above five stages.
Share via:
Tags: